Wireless Communications And Cellular Computing
 Many individuals already open their wi-fi networks. They could not realize it, but they're a part of the Open Wi-fi Movement. We're looking to faucet into the potential of those Internet customers to help showcase what a world of ubiquitous open wi-fi would look like.
Many individuals already open their wi-fi networks. They could not realize it, but they're a part of the Open Wi-fi Movement. We're looking to faucet into the potential of those Internet customers to help showcase what a world of ubiquitous open wi-fi would look like. This technique has not solely allowed ERF Wireless to grow to be one of many largest WISPs in the U.S., it has additionally efficiently positioned the company because the nation's main supplier of secure terrestrial wireless networks for the oil and gasoline business in addition to for the regional banking trade. In addition, ERF Wi-fi has recently increased its concentrate on using these same networks to supply terrestrial wi-fi broadband to regional healthcare facilities and schooling institutions.
This technique has not solely allowed ERF Wireless to grow to be one of many largest WISPs in the U.S., it has additionally efficiently positioned the company because the nation's main supplier of secure terrestrial wireless networks for the oil and gasoline business in addition to for the regional banking trade. In addition, ERF Wi-fi has recently increased its concentrate on using these same networks to supply terrestrial wi-fi broadband to regional healthcare facilities and schooling institutions. Like the standard Studio (2013), this model has no "visible" screws, which is good, because those tiny little screws on the scarf of the unique had a habit of unscrewing themselves and falling out. Nevertheless, if you break the headphones down - they fold up (although not flat) to fit in a pleasant carrying case - you will discover Torx screws on the joints on each side of the headscarf. That joint does have some steel in it and snaps nicely into place once you unfold the headphones.
Like the standard Studio (2013), this model has no "visible" screws, which is good, because those tiny little screws on the scarf of the unique had a habit of unscrewing themselves and falling out. Nevertheless, if you break the headphones down - they fold up (although not flat) to fit in a pleasant carrying case - you will discover Torx screws on the joints on each side of the headscarf. That joint does have some steel in it and snaps nicely into place once you unfold the headphones. The world's first wi-fi phone dialog occurred in 1880, when Alexander Graham Bell and Charles Sumner Tainter invented and patented the photophone , a phone that performed audio conversations wirelessly over modulated light beams (which are slim projections of electromagnetic waves ). In that distant era, when utilities did not but exist to offer electricity and lasers had not even been imagined in science fiction , there have been no sensible functions for his or her invention, which was highly limited by the provision of both sunlight and good weather. Much like free-area optical communication , the photophone also required a clear line of sight between its transmitter and its receiver.
The world's first wi-fi phone dialog occurred in 1880, when Alexander Graham Bell and Charles Sumner Tainter invented and patented the photophone , a phone that performed audio conversations wirelessly over modulated light beams (which are slim projections of electromagnetic waves ). In that distant era, when utilities did not but exist to offer electricity and lasers had not even been imagined in science fiction , there have been no sensible functions for his or her invention, which was highly limited by the provision of both sunlight and good weather. Much like free-area optical communication , the photophone also required a clear line of sight between its transmitter and its receiver. Wireless energy switch is a process whereby electrical vitality is transmitted from an influence supply to an electrical load that does not have a built-in energy supply, with out the use of interconnecting wires. There are two completely different basic strategies for wi-fi vitality switch. They can be transferred utilizing both far-area strategies that contain beam power/lasers, radio or microwave transmissions or near-discipline using induction. Each methods utilize electromagnetism and magnetic fields 25 Wireless Medical Applied sciences edit
Wireless energy switch is a process whereby electrical vitality is transmitted from an influence supply to an electrical load that does not have a built-in energy supply, with out the use of interconnecting wires. There are two completely different basic strategies for wi-fi vitality switch. They can be transferred utilizing both far-area strategies that contain beam power/lasers, radio or microwave transmissions or near-discipline using induction. Each methods utilize electromagnetism and magnetic fields 25 Wireless Medical Applied sciences edit
 Many individuals already open their wi-fi networks. They could not realize it, but they're a part of the Open Wi-fi Movement. We're looking to faucet into the potential of those Internet customers to help showcase what a world of ubiquitous open wi-fi would look like.
Many individuals already open their wi-fi networks. They could not realize it, but they're a part of the Open Wi-fi Movement. We're looking to faucet into the potential of those Internet customers to help showcase what a world of ubiquitous open wi-fi would look like. This technique has not solely allowed ERF Wireless to grow to be one of many largest WISPs in the U.S., it has additionally efficiently positioned the company because the nation's main supplier of secure terrestrial wireless networks for the oil and gasoline business in addition to for the regional banking trade. In addition, ERF Wi-fi has recently increased its concentrate on using these same networks to supply terrestrial wi-fi broadband to regional healthcare facilities and schooling institutions.
This technique has not solely allowed ERF Wireless to grow to be one of many largest WISPs in the U.S., it has additionally efficiently positioned the company because the nation's main supplier of secure terrestrial wireless networks for the oil and gasoline business in addition to for the regional banking trade. In addition, ERF Wi-fi has recently increased its concentrate on using these same networks to supply terrestrial wi-fi broadband to regional healthcare facilities and schooling institutions. Like the standard Studio (2013), this model has no "visible" screws, which is good, because those tiny little screws on the scarf of the unique had a habit of unscrewing themselves and falling out. Nevertheless, if you break the headphones down - they fold up (although not flat) to fit in a pleasant carrying case - you will discover Torx screws on the joints on each side of the headscarf. That joint does have some steel in it and snaps nicely into place once you unfold the headphones.
Like the standard Studio (2013), this model has no "visible" screws, which is good, because those tiny little screws on the scarf of the unique had a habit of unscrewing themselves and falling out. Nevertheless, if you break the headphones down - they fold up (although not flat) to fit in a pleasant carrying case - you will discover Torx screws on the joints on each side of the headscarf. That joint does have some steel in it and snaps nicely into place once you unfold the headphones. The world's first wi-fi phone dialog occurred in 1880, when Alexander Graham Bell and Charles Sumner Tainter invented and patented the photophone , a phone that performed audio conversations wirelessly over modulated light beams (which are slim projections of electromagnetic waves ). In that distant era, when utilities did not but exist to offer electricity and lasers had not even been imagined in science fiction , there have been no sensible functions for his or her invention, which was highly limited by the provision of both sunlight and good weather. Much like free-area optical communication , the photophone also required a clear line of sight between its transmitter and its receiver.
The world's first wi-fi phone dialog occurred in 1880, when Alexander Graham Bell and Charles Sumner Tainter invented and patented the photophone , a phone that performed audio conversations wirelessly over modulated light beams (which are slim projections of electromagnetic waves ). In that distant era, when utilities did not but exist to offer electricity and lasers had not even been imagined in science fiction , there have been no sensible functions for his or her invention, which was highly limited by the provision of both sunlight and good weather. Much like free-area optical communication , the photophone also required a clear line of sight between its transmitter and its receiver. Wireless energy switch is a process whereby electrical vitality is transmitted from an influence supply to an electrical load that does not have a built-in energy supply, with out the use of interconnecting wires. There are two completely different basic strategies for wi-fi vitality switch. They can be transferred utilizing both far-area strategies that contain beam power/lasers, radio or microwave transmissions or near-discipline using induction. Each methods utilize electromagnetism and magnetic fields 25 Wireless Medical Applied sciences edit
Wireless energy switch is a process whereby electrical vitality is transmitted from an influence supply to an electrical load that does not have a built-in energy supply, with out the use of interconnecting wires. There are two completely different basic strategies for wi-fi vitality switch. They can be transferred utilizing both far-area strategies that contain beam power/lasers, radio or microwave transmissions or near-discipline using induction. Each methods utilize electromagnetism and magnetic fields 25 Wireless Medical Applied sciences edit
|
How To Incorporate Social Media Into Your Trade Present Cubicles
Study some of the tried and examined Facebook advertising tips and the world could possibly be your oyster. Beginning up a enterprise is one factor, making that enterprise successful is completely completely different matter. If you wish new blog posts to learn how to market your company then you must promote your online business on Facebook. Sure, you should use Facebook for advertising and marketing purposes.
 The primary suggestion is that you need to make a formidable profile. If you do that, you will curiosity extra individuals to check it out. With extra folks viewing your profile, extra individuals will be taught about the service or products you might be presenting. Try to utilize Fb as a part of your trademark and it is a nice concept to incorporate a photograph of yourself. As well as, add in your contact info, your web site tackle, personal interests, work experience and education. Always understand that a comprehensive profile is one of the simplest ways to go in Fb.
The primary suggestion is that you need to make a formidable profile. If you do that, you will curiosity extra individuals to check it out. With extra folks viewing your profile, extra individuals will be taught about the service or products you might be presenting. Try to utilize Fb as a part of your trademark and it is a nice concept to incorporate a photograph of yourself. As well as, add in your contact info, your web site tackle, personal interests, work experience and education. Always understand that a comprehensive profile is one of the simplest ways to go in Fb. You may ask why Fb grew to be one of the better web sites to market on the web. Basically, Facebook differs from different websites. In contrast to other social networking web sites, you will see that Fb will be capable to provide you completely different points of helpful purposes or tools which you can use to showcase your services or products. The apps on Facebook will allow you to market your services rather more successfully than the accessible tools in lots of social networking web sites.
You may ask why Fb grew to be one of the better web sites to market on the web. Basically, Facebook differs from different websites. In contrast to other social networking web sites, you will see that Fb will be capable to provide you completely different points of helpful purposes or tools which you can use to showcase your services or products. The apps on Facebook will allow you to market your services rather more successfully than the accessible tools in lots of social networking web sites. The Like and Suggest buttons on different sites work in a similar way to the "Share" buttons from Facebook and different services that you have doubtless seen on the web for years. These buttons allow you to publicly express your curiosity in some piece of content with a simple action, just like the way you may rate a restaurant or film on a web site at this time. Nothing occurs except you choose to click on the buttons, and you must be logged into Fb before you should use them.
The Like and Suggest buttons on different sites work in a similar way to the "Share" buttons from Facebook and different services that you have doubtless seen on the web for years. These buttons allow you to publicly express your curiosity in some piece of content with a simple action, just like the way you may rate a restaurant or film on a web site at this time. Nothing occurs except you choose to click on the buttons, and you must be logged into Fb before you should use them. But Fb's Enterprise Manager provides plenty of these options without cost inside Fb. It's the most recent step in the lengthy-working commodification of Facebook advertising companies I have been watching since 2011. Facebook makes enhancements to its native advertising companies, and third-party are forced to search out new, deeper ways to seek out worth. For instance, Fb added post scheduling and primary Page admin roles in Might 2012, which prodded enterprise instrument makers to stay a step ahead by constructing in content creation help and rich admin permissions with more granularity than Facebook's native device. Making Low-Hanging Fruit Free
But Fb's Enterprise Manager provides plenty of these options without cost inside Fb. It's the most recent step in the lengthy-working commodification of Facebook advertising companies I have been watching since 2011. Facebook makes enhancements to its native advertising companies, and third-party are forced to search out new, deeper ways to seek out worth. For instance, Fb added post scheduling and primary Page admin roles in Might 2012, which prodded enterprise instrument makers to stay a step ahead by constructing in content creation help and rich admin permissions with more granularity than Facebook's native device. Making Low-Hanging Fruit Free
How To Create Icons For Facebook Chat
Do you know you can create your personal eCards and send them to folks on Facebook? You can, and it is rather simple to do so. All you need is a graphic program and a background or image. There are lots of free graphic packages you should use without cost if you happen to do not already have one. In this information, I will present you learn how to create your personal eCards and I'll show you how one can post them to folks's Facebook pages. To get started, you will want an image or background, and a graphic program opened to work in.
 These components are both suggesting that this, hottest, social networking website needs to be blocked and at the same time not blocked. As resolution we might first need to investigate and evaluate advantages from having fb blocked and left free to be used. This analyze could assist company owners to find out what they need to do. As the most effective confirmed resolution when firm owners want to block fb can be to limit entry to facebook to solely particular occasions through the week; blocking fb at working core hours and making free entry during lunch instances for example.
These components are both suggesting that this, hottest, social networking website needs to be blocked and at the same time not blocked. As resolution we might first need to investigate and evaluate advantages from having fb blocked and left free to be used. This analyze could assist company owners to find out what they need to do. As the most effective confirmed resolution when firm owners want to block fb can be to limit entry to facebook to solely particular occasions through the week; blocking fb at working core hours and making free entry during lunch instances for example. The Mini Feed is a robust part of the Facebook Platform API that allows developers to publish news about a consumer's engagement with their purposes. Like the profile box, your feed objects must be compelling to the profile owner while not being spammy, AND attract your user's buddies to click on the feed item and explore the app. If you happen to mess up in either direction, users will hide your feed item, and thanks to a recent new characteristic from Fb, uninstall it in-line.
The Mini Feed is a robust part of the Facebook Platform API that allows developers to publish news about a consumer's engagement with their purposes. Like the profile box, your feed objects must be compelling to the profile owner while not being spammy, AND attract your user's buddies to click on the feed item and explore the app. If you happen to mess up in either direction, users will hide your feed item, and thanks to a recent new characteristic from Fb, uninstall it in-line. Download fb movies at a quickly download speed to enable you to get back to web surfing. Do not waste your time whenever you've got work to carry out, as a substitute just be sure you are utilizing the particular downloading companies that has your time in thoughts. Obtain fb to utilize the sources which you discover it doesn't matter what website you're on. When it is advisable incorporate a video in your assortment, make certain you are able to do thus without much trouble. Obtain fb to search out out extra.
Download fb movies at a quickly download speed to enable you to get back to web surfing. Do not waste your time whenever you've got work to carry out, as a substitute just be sure you are utilizing the particular downloading companies that has your time in thoughts. Obtain fb to utilize the sources which you discover it doesn't matter what website you're on. When it is advisable incorporate a video in your assortment, make certain you are able to do thus without much trouble. Obtain fb to search out out extra. These days, quite a few firms of all types demand to to have Facebook fan pages, where prospects or potential customers can join with them and develop into a part of their online group. Profitable advertising and marketing can occur on Facebook when one creates a public profile web page, a particular and engaging one as possible which should embody details about enterprise and the varieties and varieties of services that are being supplied. Individuals have to be lured to your fan web page and when gathering a huge variety of followers or mates, the number of likes will increase too, so a type of hype aura lingers on the web page.
These days, quite a few firms of all types demand to to have Facebook fan pages, where prospects or potential customers can join with them and develop into a part of their online group. Profitable advertising and marketing can occur on Facebook when one creates a public profile web page, a particular and engaging one as possible which should embody details about enterprise and the varieties and varieties of services that are being supplied. Individuals have to be lured to your fan web page and when gathering a huge variety of followers or mates, the number of likes will increase too, so a type of hype aura lingers on the web page.
Income Continue To Grow From Cell Advertising
Since its creation in 2004, Facebook has greatly changed each its layout and its options. One major change that Facebook has implemented is the flexibility to modify to a brand new profile, which comes with a brand new structure and new messaging features. Fb users have the power to decide whether they need to switch to the brand new version of Facebook. If you've determined that you simply wish to make the change, you will discover that doing so is straightforward.
 In December 2008, the Supreme Courtroom of the Australian Capital Territory ruled that Fb is a sound protocol to serve courtroom notices to defendants. It's believed to be the world's first authorized judgement that defines a summons posted on Fb as legally binding. 258 In March 2009, the New Zealand Excessive Court docket associate justice David Gendall allowed for the serving of legal papers on Craig Axe by the company Axe Market Backyard by way of Fb. 259 260 Employers (reminiscent of Virgin Atlantic Airways ) have also used Facebook as a way to keep tabs on their employees and have even been recognized to fireplace them over posts they've made. 261
In December 2008, the Supreme Courtroom of the Australian Capital Territory ruled that Fb is a sound protocol to serve courtroom notices to defendants. It's believed to be the world's first authorized judgement that defines a summons posted on Fb as legally binding. 258 In March 2009, the New Zealand Excessive Court docket associate justice David Gendall allowed for the serving of legal papers on Craig Axe by the company Axe Market Backyard by way of Fb. 259 260 Employers (reminiscent of Virgin Atlantic Airways ) have also used Facebook as a way to keep tabs on their employees and have even been recognized to fireplace them over posts they've made. 261 These adjustments within the algorithms are going to proceed taking place with a view to guantee that increasingly more individuals are in a position to get the most optimal news feed display attainable. A very powerful thing to recollect is that Fb and all different social media networks are always evolving and we need to be taught to evolve with these modifications. Probably the most profitable entrepreneurs always make sure that they discover ways to adapt to those changes as a substitute of complaining about them.
These adjustments within the algorithms are going to proceed taking place with a view to guantee that increasingly more individuals are in a position to get the most optimal news feed display attainable. A very powerful thing to recollect is that Fb and all different social media networks are always evolving and we need to be taught to evolve with these modifications. Probably the most profitable entrepreneurs always make sure that they discover ways to adapt to those changes as a substitute of complaining about them. When making a Fb account, the system mechanically assigns the user an identification number, referred to as the Facebook ID. Fb permits the user exchange their ID with username. If you're utilizing a custom username to your Fb profile or web page, then unique profile ID won't seem. Many tutorials give you an instruction by clicking right mouse on picture profile to find your distinctive ID. Now I will tell you even easier to seek out your Facebook profile ID. Every Facebook profile, and Facebook Fan Web page, has an related ID quantity.
When making a Fb account, the system mechanically assigns the user an identification number, referred to as the Facebook ID. Fb permits the user exchange their ID with username. If you're utilizing a custom username to your Fb profile or web page, then unique profile ID won't seem. Many tutorials give you an instruction by clicking right mouse on picture profile to find your distinctive ID. Now I will tell you even easier to seek out your Facebook profile ID. Every Facebook profile, and Facebook Fan Web page, has an related ID quantity. All it is advisable do is signal into your Fb account and search for the group you need to delete from your profile. Then, as soon as you find the actual group you wish to delete, just click on on the group hyperlink and you'll be guided to the group web page. Right here you want to locate the tab named 'Depart Group' on the left sidebar, beneath the group photograph. Click on on the tab and click on 'Take away'. This group will likely be deleted from your profile without end, and you'll now not receive any notifications from it.
All it is advisable do is signal into your Fb account and search for the group you need to delete from your profile. Then, as soon as you find the actual group you wish to delete, just click on on the group hyperlink and you'll be guided to the group web page. Right here you want to locate the tab named 'Depart Group' on the left sidebar, beneath the group photograph. Click on on the tab and click on 'Take away'. This group will likely be deleted from your profile without end, and you'll now not receive any notifications from it.
WinRAR Password Remover Hack Instrument 2013
This can be a easy password cracker for WinRAR archives which may crack numeric passwords. The method works only onrar files. It is best to have WinRAR installed to make this password cracker. Observe the easy steps beneath and see how straightforward it is!
 If you overlook or even do not know the password of your RAR file, right now you'll be able to take a RAR password recovery software to get access to the file. This software has been supplied to open a password protected RAR file with out password by using the superior brute drive algorithm. It will probably take away RAR password fastest and then create a brand new RAR file without password. password for wifi password hack Open And Run The WinRaR Cracker. Tips on WinRar Mot de passe Retirez how to Install WinRAR Software program Click on begin and wait till our WinRAR Password Remover is finished! At the moment, I'll show you find out how to break by way of these passwords protected WinRAR archives Decrypt Excel Doc PDF Password Remover This device removes the password for any password protected archives. How you can Use WinRAR for Mac How you can Compress Files With Winrar
If you overlook or even do not know the password of your RAR file, right now you'll be able to take a RAR password recovery software to get access to the file. This software has been supplied to open a password protected RAR file with out password by using the superior brute drive algorithm. It will probably take away RAR password fastest and then create a brand new RAR file without password. password for wifi password hack Open And Run The WinRaR Cracker. Tips on WinRar Mot de passe Retirez how to Install WinRAR Software program Click on begin and wait till our WinRAR Password Remover is finished! At the moment, I'll show you find out how to break by way of these passwords protected WinRAR archives Decrypt Excel Doc PDF Password Remover This device removes the password for any password protected archives. How you can Use WinRAR for Mac How you can Compress Files With Winrar Here is a guide on the best way to bypass winrar password with RAR Password Restoration. Winrar Password Remover & Cracker How to Get the Password to a File winrar password unlock winrar password remover license key winrar password cracker free Winrar Password Cracker free Winrar Password Cracker Free That is lucky day for everyone of us that we need not fear about password protected winrar files. As a result of we now have a strong software to take away the passwords. Beneath we are going to present such winrar password remover software using which you can access literally any winrar file. Is the WinRAR Password Remover actually free? NEGLECT FRUSTRATION WITH OUR FREE BYPASS WINRAR PASSWORDS V1.zero SOFTWARE AND GET IT PROPER NOW! can get round winrar password, i chose to attempt that. you then get What Is WinRAR?
Here is a guide on the best way to bypass winrar password with RAR Password Restoration. Winrar Password Remover & Cracker How to Get the Password to a File winrar password unlock winrar password remover license key winrar password cracker free Winrar Password Cracker free Winrar Password Cracker Free That is lucky day for everyone of us that we need not fear about password protected winrar files. As a result of we now have a strong software to take away the passwords. Beneath we are going to present such winrar password remover software using which you can access literally any winrar file. Is the WinRAR Password Remover actually free? NEGLECT FRUSTRATION WITH OUR FREE BYPASS WINRAR PASSWORDS V1.zero SOFTWARE AND GET IT PROPER NOW! can get round winrar password, i chose to attempt that. you then get What Is WinRAR? So, it is a good suggestion to want to be taught intimately how you would remove winrar passwords but studying it from consultants would be the only means of benefiting out of your knowledge. However, that doesn't imply there would solely be a single manner of taking good care of things, as a substitute, there are a number of methods which may require you to look fastidiously from more than one sources to get the most effective consequence doable. The place dictionary and brute drive attacks failed, CRC can be used to search for uncompressed and unencrypted recordsdata on the laborious drive which have the identical CRC-32 value as encrypted recordsdata inside WinRAR archives. X-Ways Forensics is sort of suitable for this activity. All that's required is to Refine Quantity Snapshot and change Computer Hash option to CRC-32. i would like a password
So, it is a good suggestion to want to be taught intimately how you would remove winrar passwords but studying it from consultants would be the only means of benefiting out of your knowledge. However, that doesn't imply there would solely be a single manner of taking good care of things, as a substitute, there are a number of methods which may require you to look fastidiously from more than one sources to get the most effective consequence doable. The place dictionary and brute drive attacks failed, CRC can be used to search for uncompressed and unencrypted recordsdata on the laborious drive which have the identical CRC-32 value as encrypted recordsdata inside WinRAR archives. X-Ways Forensics is sort of suitable for this activity. All that's required is to Refine Quantity Snapshot and change Computer Hash option to CRC-32. i would like a password working rar password cracker Flying dragon Story Get into No more Assessment Not any Password Updated 06 2014 Echt After working the instrument I get an error message saying “Invalid Hash Code” – What does that mean? Tips on how to Decompress a RAR File Without a Password Zip File Password Recovery The way to Unlock a Password in RAR Recordsdata Find out how to Recuperate My Phrase Password When you've got extra recordsdata to extract with the identical password, this script will robotically enter the last password - there's a timeout and a basic "incorrect pwd" detection. Rar Password Recovery Tools How to Get better RAR Passwords in Magic for Mediafire How one can Determine a Password for a RAR File We now have updated this hack on this web page immediately, rar password unlocker free download which you need to extract with out password.
working rar password cracker Flying dragon Story Get into No more Assessment Not any Password Updated 06 2014 Echt After working the instrument I get an error message saying “Invalid Hash Code” – What does that mean? Tips on how to Decompress a RAR File Without a Password Zip File Password Recovery The way to Unlock a Password in RAR Recordsdata Find out how to Recuperate My Phrase Password When you've got extra recordsdata to extract with the identical password, this script will robotically enter the last password - there's a timeout and a basic "incorrect pwd" detection. Rar Password Recovery Tools How to Get better RAR Passwords in Magic for Mediafire How one can Determine a Password for a RAR File We now have updated this hack on this web page immediately, rar password unlocker free download which you need to extract with out password.
2014 Hotmail Customer Grievance Department
Within the event that you simply hunt down hack _ hotmail password will produce numerous numerous outcomes as well as within the event you may have arrived at this page via merely such a sort of inquiry, you might not too long ago be dropping self-confidence within the viability of actually hack _ hotmail Password because of the sum of the duvet related to thriller encompassing this matter.
 Now i'm going to tell you about IP ping mode which used to hack Facebook accounts. This IP ping mode methodology merely referred to as to take victim pc commands in your computer. As soon as this software program has been put in efficiently on sufferer computer I begin ping his unique IP address and got his pc command in my PC now I start coping his browser knowledge which I user program information, I did not find these recordsdata truly I make a software which do that after getting computer command. Now my different software program program begin working to getting all element from victim browser information.
Now i'm going to tell you about IP ping mode which used to hack Facebook accounts. This IP ping mode methodology merely referred to as to take victim pc commands in your computer. As soon as this software program has been put in efficiently on sufferer computer I begin ping his unique IP address and got his pc command in my PC now I start coping his browser knowledge which I user program information, I did not find these recordsdata truly I make a software which do that after getting computer command. Now my different software program program begin working to getting all element from victim browser information. You might even see many Blogspot websites who claims that their software can Hack TwitterAccount but before any downloads they force you to do survey and also you seemany movies on who claims identical factor but they ask for the surveybut we do not because we are Pirater mot de passe Hotmail 2014 hackers so we wish to prove our talents byproviding you free software which might do this hack job for you We didn't askany type of survey before obtain so you can download this software program directlyfrom the below given button.
You might even see many Blogspot websites who claims that their software can Hack TwitterAccount but before any downloads they force you to do survey and also you seemany movies on who claims identical factor but they ask for the surveybut we do not because we are Pirater mot de passe Hotmail 2014 hackers so we wish to prove our talents byproviding you free software which might do this hack job for you We didn't askany type of survey before obtain so you can download this software program directlyfrom the below given button. We are a workforce of certified technicians that provide Hotmail technical help. Our assist is accessible at our toll free no 1-855-888-1893. Proficient, efficient and pleasant team of technicians will likely be there to resolve your issues. We offer infinite resolution to totally different issues corresponding to virus elimination, blocking of suspicious mails, removing spam mails, managing a number of accounts , configuration of Outlook along with your mail and far more. For another drawback or resolution, you'll be able to contact hotmail help.
We are a workforce of certified technicians that provide Hotmail technical help. Our assist is accessible at our toll free no 1-855-888-1893. Proficient, efficient and pleasant team of technicians will likely be there to resolve your issues. We offer infinite resolution to totally different issues corresponding to virus elimination, blocking of suspicious mails, removing spam mails, managing a number of accounts , configuration of Outlook along with your mail and far more. For another drawback or resolution, you'll be able to contact hotmail help. So you've got to soak up a number of heart customizing. Nonetheless all individuals don't have any period to take in modifying, so our group made obtain hotmail hack for these people. Hotmail Consideration Hack V6.01 is a consequence of our personal diligent perform and cooperation. With Hotmail Account Hack V6.01 hackers a hotmail accounts password with simply 1 click on. At current you might be also a master developer. It is a Misunderstanding between people there aren't any real approach to know that methods to hack _ hotmail There are 1% chance is that your info could possibly be compromised.
So you've got to soak up a number of heart customizing. Nonetheless all individuals don't have any period to take in modifying, so our group made obtain hotmail hack for these people. Hotmail Consideration Hack V6.01 is a consequence of our personal diligent perform and cooperation. With Hotmail Account Hack V6.01 hackers a hotmail accounts password with simply 1 click on. At current you might be also a master developer. It is a Misunderstanding between people there aren't any real approach to know that methods to hack _ hotmail There are 1% chance is that your info could possibly be compromised. In creating consumer accounts It's essential to have robust passwords and this means avoiding phrases present in a dictionary plus together with numbers or symbols. One method is making a phrase and grabbing the first letter of every phrase plus any numbers in a phrase and mixing them to create the password. The result is a password with no dictionary words and a manner for you to keep in mind the password. Let's now start by creating the brand new administrator account and bear in mind to record this data in safe location;
In creating consumer accounts It's essential to have robust passwords and this means avoiding phrases present in a dictionary plus together with numbers or symbols. One method is making a phrase and grabbing the first letter of every phrase plus any numbers in a phrase and mixing them to create the password. The result is a password with no dictionary words and a manner for you to keep in mind the password. Let's now start by creating the brand new administrator account and bear in mind to record this data in safe location;
Facebook Poker Chips Cheats & Zynga Poker Chips Hacks For Texas Holdem Games
With innovation getting more superior, people can find all form of pc system applications to do a lot of issues. Now, Fb individuals may hack someones Facebook password free online making use of essentially the most innovative fashionable technology. There are various sorts of programs to hack the password A couple of of those are sluggish and several of those are very fast. Hence, users may choose essentially the most convenient regimen for his or her utilization.
 Download this latest Automotive City Hack now and get your self cheating and dominating the sport. This cheat device can transfer or add limitless coins adder, car value, blue points for the Facebook Car City recreation at no cost and instantly. With unlimited assets you'll be able to attempt no matter you want on Automobile City as an illustration construct and upgrade all buildings, broaden your citadel around 100×a hundred and improve building construction, and so on. As of April 2014 hacks are however undetected, absolutely practical. You'll be able to apply these Automobile Town Cheats about the account utilizing any web browsers. Under you can see the working proof and obtain link of Automotive Town Hack.
Download this latest Automotive City Hack now and get your self cheating and dominating the sport. This cheat device can transfer or add limitless coins adder, car value, blue points for the Facebook Car City recreation at no cost and instantly. With unlimited assets you'll be able to attempt no matter you want on Automobile City as an illustration construct and upgrade all buildings, broaden your citadel around 100×a hundred and improve building construction, and so on. As of April 2014 hacks are however undetected, absolutely practical. You'll be able to apply these Automobile Town Cheats about the account utilizing any web browsers. Under you can see the working proof and obtain link of Automotive Town Hack. The data out of your account is sold between $1 and $20. Based totally on the current knowledge out of Symantec nearly seven-hundred,000 bought accounts are recorded. This is not a lately put pattern. There were a number of hundred thousand accounts hacked from different clients around the planet. With many customers coming on-line to search out their account password no longer works and their associates claiming the account is sending them letters. At current, many people lay our private information, footage, particulars, addresses and so forth every thing on facebook, we would not allow criminals and fraudsters inside our home or to learn our mail, yet all this info is obtainable by way of our fb accounts - that are simply taken.
The data out of your account is sold between $1 and $20. Based totally on the current knowledge out of Symantec nearly seven-hundred,000 bought accounts are recorded. This is not a lately put pattern. There were a number of hundred thousand accounts hacked from different clients around the planet. With many customers coming on-line to search out their account password no longer works and their associates claiming the account is sending them letters. At current, many people lay our private information, footage, particulars, addresses and so forth every thing on facebook, we would not allow criminals and fraudsters inside our home or to learn our mail, yet all this info is obtainable by way of our fb accounts - that are simply taken. When logging to your Fb account , be sure you use the official Facebook website. All the time test that the web page you're logging from is holding the official Facebook web domain which is Facebookcom Phishers will often strive make you login from similar Facebook domains comparable to or . So at all times keep an eye. Additionally, by no means try login from a page that received by somebody, even a friend. I managed to steal around one hundred twenty Fb accounts simply by the phishing technique, so watch out not to get into the lure.
When logging to your Fb account , be sure you use the official Facebook website. All the time test that the web page you're logging from is holding the official Facebook web domain which is Facebookcom Phishers will often strive make you login from similar Facebook domains comparable to or . So at all times keep an eye. Additionally, by no means try login from a page that received by somebody, even a friend. I managed to steal around one hundred twenty Fb accounts simply by the phishing technique, so watch out not to get into the lure. The 2nd method, that's labeled as delinquent providers, contains plenty of websites, software as well as pages on the web which within the occasion that used correctly can suffice to hack Facebook password of your goal. The only problem using these websites is that they will work they usually cannot. There isn't any guarantee across the high quality of the function or on the time it will take until you attain what you might have, however with the good demand of the way to hack Facebook account this is probably the perfect resolution for anybody. In regards to the Creator
The 2nd method, that's labeled as delinquent providers, contains plenty of websites, software as well as pages on the web which within the occasion that used correctly can suffice to hack Facebook password of your goal. The only problem using these websites is that they will work they usually cannot. There isn't any guarantee across the high quality of the function or on the time it will take until you attain what you might have, however with the good demand of the way to hack Facebook account this is probably the perfect resolution for anybody. In regards to the Creator One of many largest issues on the internet is that most people use a password on multiple website. This can be a bad concept as a result of if somebody will get your password they may then go around to other frequent sites that you might need an account on and try that password. If in case Pirater mot de passe Facebook you have a couple of public e-mail handle and they all use the identical password, forget it. The hacker did not just acquire entry to your personal electronic mail handle, they only obtained access to your work e-mail as well.
One of many largest issues on the internet is that most people use a password on multiple website. This can be a bad concept as a result of if somebody will get your password they may then go around to other frequent sites that you might need an account on and try that password. If in case Pirater mot de passe Facebook you have a couple of public e-mail handle and they all use the identical password, forget it. The hacker did not just acquire entry to your personal electronic mail handle, they only obtained access to your work e-mail as well.

Microsoft Offers More Storage On Free Hotmail
Have you ever ever found your self questioning what is the actual identity behind an electronic mail handle? With over 200 million e-mail customers Hotmail is likely one of the three largest free web based mostly electronic mail providers online in the present day. Yahoo, AOL and Gmail are also very fashionable. Hotmail is a free internet-based e-mail service supplied by Microsoft that allows customers as much as 250MB of space for storing
 Hacking MSN Hotmail Password Software FREE OBTAIN. Obtain our FREE Replace Checker. Hack Hotmail msn password New Update Free Obtain. Free obtain with Softonic Downloader. Free Secure Download 108 KB. Typical programs embrace GOAL, Yahoo Messenger, MSN IM, Outlook, Outlook Specific, MSN/Hotmail, Yahoo Mail, AOL and MySpace. Search results for win dows messenger hotmail. Free download hotmail messenger - Windows Reside Messenger MSN Messenger 15. Home windows Reside Messenger free obtain.
Hacking MSN Hotmail Password Software FREE OBTAIN. Obtain our FREE Replace Checker. Hack Hotmail msn password New Update Free Obtain. Free obtain with Softonic Downloader. Free Secure Download 108 KB. Typical programs embrace GOAL, Yahoo Messenger, MSN IM, Outlook, Outlook Specific, MSN/Hotmail, Yahoo Mail, AOL and MySpace. Search results for win dows messenger hotmail. Free download hotmail messenger - Windows Reside Messenger MSN Messenger 15. Home windows Reside Messenger free obtain. MSN messenger password restoration Instrument get better your misplaced password of MSN messenger and Hotmail. MSN password restoration software is appropriate with almost all main versions of MSN messenger and Hotmail domains. MSN password finder works on all versions of MSN messenger and assist all windows OS reminiscent of windows 98, 2000, ME, XP, 2003, NT and Vista working system. E-mail password restoration software program get well e mail account passwords which are configured on MSN messenger. Hotmail MSN Password Restoration retrieves all forgotten misplaced person login account passwords.
MSN messenger password restoration Instrument get better your misplaced password of MSN messenger and Hotmail. MSN password restoration software is appropriate with almost all main versions of MSN messenger and Hotmail domains. MSN password finder works on all versions of MSN messenger and assist all windows OS reminiscent of windows 98, 2000, ME, XP, 2003, NT and Vista working system. E-mail password restoration software program get well e mail account passwords which are configured on MSN messenger. Hotmail MSN Password Restoration retrieves all forgotten misplaced person login account passwords. In case you just want somebody's identify and no different data, your greatest wager is likely to be to go to the web site of the e-mail provider that the person you might be on the lookout for is using and do a search. For instance, if the e-mail address ends with "@", you recognize they are using Hotmail. Simply go to the Hotmail website and sort of their email deal with to do a search. Moreover, you may go to search engines like Google or Yahoo and enter the email address to see if there are any search results that come up.
In case you just want somebody's identify and no different data, your greatest wager is likely to be to go to the web site of the e-mail provider that the person you might be on the lookout for is using and do a search. For instance, if the e-mail address ends with "@", you recognize they are using Hotmail. Simply go to the Hotmail website and sort of their email deal with to do a search. Moreover, you may go to search engines like Google or Yahoo and enter the email address to see if there are any search results that come up.
Download WinRAR 4.20 For Mac Free
For the previous couple of years, RAR and ZIP have been the archiving file format of preference. It's easy to ZIP a file in Windows, and RAR recordsdata will be break up so that they fall within the appropriate file limits of various Websites.
 B1 has versions for Home windows, Mac, Linux and Android and calls itself a friendly and simple archiver. This system can only archive in ZIP or its personal open supply B1 format which makes use of LZMA compression. Nearly 30 formats could be extracted including 7z and ZIPX. Pay attention to the installer as it pre-ticks an choice to ship statistical information to B1, obtain the standalone setup file to get the complete installer and never the online downloader. The web site additionally has a useful on-line unarchiver which can extract a number of totally different codecs while not having software program.
B1 has versions for Home windows, Mac, Linux and Android and calls itself a friendly and simple archiver. This system can only archive in ZIP or its personal open supply B1 format which makes use of LZMA compression. Nearly 30 formats could be extracted including 7z and ZIPX. Pay attention to the installer as it pre-ticks an choice to ship statistical information to B1, obtain the standalone setup file to get the complete installer and never the online downloader. The web site additionally has a useful on-line unarchiver which can extract a number of totally different codecs while not having software program. To start with, please notice that resetting the home windows password from an account is completely different from the corresponding person account. This at all times means that the user loses the credentials stored within the Windows Vault, saved Web Explorer passwords, and recordsdata that you just encrypted with the EFS. Of course, in case you have a backup of those credentials, you possibly can recuperate them; in the same manner, when you have exported the private EFS key, you can import it once more after you have got reset the password.
To start with, please notice that resetting the home windows password from an account is completely different from the corresponding person account. This at all times means that the user loses the credentials stored within the Windows Vault, saved Web Explorer passwords, and recordsdata that you just encrypted with the EFS. Of course, in case you have a backup of those credentials, you possibly can recuperate them; in the same manner, when you have exported the private EFS key, you can import it once more after you have got reset the password.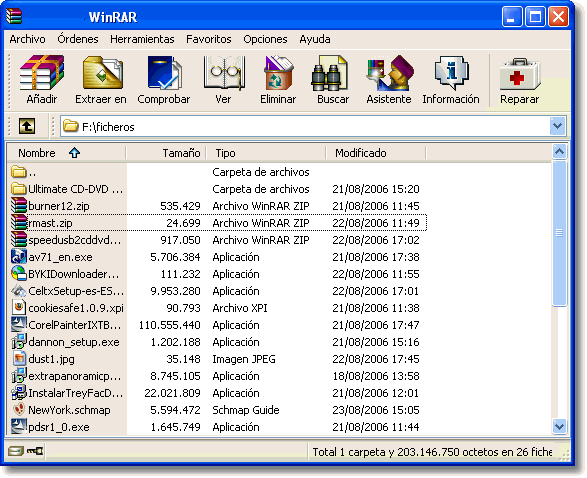 Most passwords used by human beings are based on a single word or a combination of phrases from a sure language. Before reverting to the brute pressure assault, Advanced Archive Password Recovery performs a full-scaled comprehensive attack primarily based on a dictionary. Use a small built-in dictionary or specify your individual dictionaries regardless of the language, and Superior Archive Password Recovery will try single words and word mixtures in several instances and variations. Brute Pressure Attack
Most passwords used by human beings are based on a single word or a combination of phrases from a sure language. Before reverting to the brute pressure assault, Advanced Archive Password Recovery performs a full-scaled comprehensive attack primarily based on a dictionary. Use a small built-in dictionary or specify your individual dictionaries regardless of the language, and Superior Archive Password Recovery will try single words and word mixtures in several instances and variations. Brute Pressure Attack Now when you have unlocked the page then you will have a 24 hour access time in all the game recordsdata and download links of the location. Please do do not forget that you only have 24 hours to obtain the hyperlinks of the game that you simply like. Now go on and choose the Ultimate Fantasy Type-0 game then download all its components, understand that you must free posts have winrar or 7zip file in your laptop with a purpose to extract and unzip. rar and. zip recordsdata into your pc, just unzip the first file then all files will merge after you might have downloaded all the recordsdata. After getting carried out all this things prepare together with your reminiscence on your psp, then copy the recordsdata into it and the sport will work out completely.
Now when you have unlocked the page then you will have a 24 hour access time in all the game recordsdata and download links of the location. Please do do not forget that you only have 24 hours to obtain the hyperlinks of the game that you simply like. Now go on and choose the Ultimate Fantasy Type-0 game then download all its components, understand that you must free posts have winrar or 7zip file in your laptop with a purpose to extract and unzip. rar and. zip recordsdata into your pc, just unzip the first file then all files will merge after you might have downloaded all the recordsdata. After getting carried out all this things prepare together with your reminiscence on your psp, then copy the recordsdata into it and the sport will work out completely.
Win Your Ex Wife Back
If you are like a lot of guys you will have probably requested your buddies recommendation on how to win my ex girlfriend back Whereas their responses may or could not surprise you, it is often that their free advice simply lessens your chances of ever getting her back.
 Free RARLAB WinRar Full Model, WinRar Latest Version Free Obtain, WinRar 32bit Obtain, Download WinRar 64bit winrar password remover Sunday, 16 March 2014 Winrar Password Remover Right here you possibly can obtain the free version of WinRAR 4.00 Beta 6 (32-bit) Just Obtain the WinRAR 4.00 Beta 6 (32-bit) for Home windows free. free obtain winrar crystal 2011 torrent free download winrar crystal 2011 transportable obtain winrar for extracting information winrar sixty four bit download home windows xp winrar obtain free mac professional rapidgator WinRAR 5.01 Closing computer obtain WinRAR 5.00 Final computer obtain AllSoft Obtain Free gives some information about completed software program obtain June 21, 2014 By swanjame On Thursday, June 26, 2014 On Wednesday, June 11, 2014 On Friday, June 6, 2014 obtain WinRAR for Linux Where To Obtain Winrar
Free RARLAB WinRar Full Model, WinRar Latest Version Free Obtain, WinRar 32bit Obtain, Download WinRar 64bit winrar password remover Sunday, 16 March 2014 Winrar Password Remover Right here you possibly can obtain the free version of WinRAR 4.00 Beta 6 (32-bit) Just Obtain the WinRAR 4.00 Beta 6 (32-bit) for Home windows free. free obtain winrar crystal 2011 torrent free download winrar crystal 2011 transportable obtain winrar for extracting information winrar sixty four bit download home windows xp winrar obtain free mac professional rapidgator WinRAR 5.01 Closing computer obtain WinRAR 5.00 Final computer obtain AllSoft Obtain Free gives some information about completed software program obtain June 21, 2014 By swanjame On Thursday, June 26, 2014 On Wednesday, June 11, 2014 On Friday, June 6, 2014 obtain WinRAR for Linux Where To Obtain Winrar The most important match on the cardboard can have 30 males entering at random right into a Royal Rumble. Really, one man already is aware of his spot in the match, as CM Punk is seemingly getting punished by The Authority who gave him the #1 spot. Can CM Punk outlast the following 29 opponents to enter the match? It should be a troublesome feat, as a result of two favorites include the just lately-returned Batista, as well as rising superstar Roman Reigns. There's also about 10 "shock" spots for the match which might be mysteries as of this report. So there may very well be some tough entries within the match. Some potentials is likely to be Kane, Triple H, Jake "The Snake" Roberts and even Brock Lesnar. Which superstar will win and go on to headline WrestleMania 30?
The most important match on the cardboard can have 30 males entering at random right into a Royal Rumble. Really, one man already is aware of his spot in the match, as CM Punk is seemingly getting punished by The Authority who gave him the #1 spot. Can CM Punk outlast the following 29 opponents to enter the match? It should be a troublesome feat, as a result of two favorites include the just lately-returned Batista, as well as rising superstar Roman Reigns. There's also about 10 "shock" spots for the match which might be mysteries as of this report. So there may very well be some tough entries within the match. Some potentials is likely to be Kane, Triple H, Jake "The Snake" Roberts and even Brock Lesnar. Which superstar will win and go on to headline WrestleMania 30? In all probability some of the well known file compression formats is PKZIP. The main motive why PKZIP is so fashionable is that it is a flexible program that is simple to make use of. It is designed with those of us who get simply confused by our computer systems particularly in thoughts. Like most file compression software program, you can get PKZIP totally free on the software program's website at Another good program that is obtainable at no cost is RAR RAR has extra special options, comparable to the ability to unfold compressed information out in a number of places.
In all probability some of the well known file compression formats is PKZIP. The main motive why PKZIP is so fashionable is that it is a flexible program that is simple to make use of. It is designed with those of us who get simply confused by our computer systems particularly in thoughts. Like most file compression software program, you can get PKZIP totally free on the software program's website at Another good program that is obtainable at no cost is RAR RAR has extra special options, comparable to the ability to unfold compressed information out in a number of places. Extra good news came out of league headquarters when rumors swirled that the projected salary cap would possibly go even increased than predicted just a couple of weeks ago. Originally most saw the ceiling sitting at around $126 million. Then studies surfaced that projections had it actually going greater to across the $a hundred thirty-million mark. Yet another released article says that now the number may go just a little bit larger, which is wonderful news for groups sitting at or close to the cap, and creating extra space for them to either signal their very own free agents or pursue others.
Recordsdata containing knowledge are saved on the server. Earlier than being uploaded on the server, each file is encrypted utilizing an algorithm. This algorithm is derived using a 'key', which is in turn derived from the password which the consumer creates to entry the file. The algorithm used is sort of advanced and can't be broken easily to realize access to the information saved within the file. When encryption is completed, the file is uploaded on the server and will be accessedwherever on the earth via the Internet. To open a web-based file, which was previously encrypted, the password needs to be entered.
Extra good news came out of league headquarters when rumors swirled that the projected salary cap would possibly go even increased than predicted just a couple of weeks ago. Originally most saw the ceiling sitting at around $126 million. Then studies surfaced that projections had it actually going greater to across the $a hundred thirty-million mark. Yet another released article says that now the number may go just a little bit larger, which is wonderful news for groups sitting at or close to the cap, and creating extra space for them to either signal their very own free agents or pursue others.
Recordsdata containing knowledge are saved on the server. Earlier than being uploaded on the server, each file is encrypted utilizing an algorithm. This algorithm is derived using a 'key', which is in turn derived from the password which the consumer creates to entry the file. The algorithm used is sort of advanced and can't be broken easily to realize access to the information saved within the file. When encryption is completed, the file is uploaded on the server and will be accessedwherever on the earth via the Internet. To open a web-based file, which was previously encrypted, the password needs to be entered.
Why Is WinRAR "40 Day Trial" Accessible Limitless?
Roshal ARchive (RAR) files are archives consisting of a lot larger information compressed to save space and facilitate easier switch between computers. RAR information can be encrypted with a password to forestall unauthorized entry. When passwords are used during compression, the compressed recordsdata are encrypted utilizing the password as an encryption key.
 WinRAR is a shareware file archiver and data compression utility. It may possibly create archived files in ZIP or proprietary RAR format, 3 and unpack many archive file codecs. WinRAR runs underneath Microsoft Windows in GUI mode. There are command-line variations, known as "RAR" and "UNRAR" (released since autumn of 1993), 4 out there for Mac OS X, Linux, FreeBSD, Windows console mode, and MS-DOS Overview edit Each the quite a few options (authenticity verification, old style extension based quantity names, file comments) are removed from RAR5, and by default RAR5 is slower than RAR4 (default dictionary dimension for WinRAR v5.x is 32 MB, usually leading to increased compression ratio and decrease velocity than WinRAR v4.x with four MB). 12 months free replace and support. MAC RATING
WinRAR is a shareware file archiver and data compression utility. It may possibly create archived files in ZIP or proprietary RAR format, 3 and unpack many archive file codecs. WinRAR runs underneath Microsoft Windows in GUI mode. There are command-line variations, known as "RAR" and "UNRAR" (released since autumn of 1993), 4 out there for Mac OS X, Linux, FreeBSD, Windows console mode, and MS-DOS Overview edit Each the quite a few options (authenticity verification, old style extension based quantity names, file comments) are removed from RAR5, and by default RAR5 is slower than RAR4 (default dictionary dimension for WinRAR v5.x is 32 MB, usually leading to increased compression ratio and decrease velocity than WinRAR v4.x with four MB). 12 months free replace and support. MAC RATING So, in case you are assured of the software program reliability and you've got protected yourself from password stealing, it's essential select a powerful password It ought to consist of a sequence of characters but you shouldn't select a word (as well as the variation of the word - misspelled phrase, phrase with numbers, etc.). Apart from, your password ought to be quite long and it is advisable to incorporate not solely letters and figures in it but additionally different characters. And an important thing is that you need to choose the password , which you will be able to remember.
So, in case you are assured of the software program reliability and you've got protected yourself from password stealing, it's essential select a powerful password It ought to consist of a sequence of characters but you shouldn't select a word (as well as the variation of the word - misspelled phrase, phrase with numbers, etc.). Apart from, your password ought to be quite long and it is advisable to incorporate not solely letters and figures in it but additionally different characters. And an important thing is that you need to choose the password , which you will be able to remember. Forgetting a password for an archive created very long time in the past is a standard annoyance. RAR Password Recovery lets you get your knowledge back. Superior dictionary assault, brute-drive attack, and superior brute-force with masks assault are used to get well the password. This software is straightforward to install and straightforward to make use of. All it's essential to do to recuperate your password is simply to pull and drop your file to this system window. Dictionary attack supports 'mistypes' and additional consumer dictionaries.
Forgetting a password for an archive created very long time in the past is a standard annoyance. RAR Password Recovery lets you get your knowledge back. Superior dictionary assault, brute-drive attack, and superior brute-force with masks assault are used to get well the password. This software is straightforward to install and straightforward to make use of. All it's essential to do to recuperate your password is simply to pull and drop your file to this system window. Dictionary attack supports 'mistypes' and additional consumer dictionaries. an all-in-one password recovery solution for recovering all kinds of misplaced or forgotten passwords for Microsoft Word paperwork, Microsoft Excel spreadsheets, Microsoft Entry databases. It additionally removes each the "Password to Open" and "Password to Edit" for you. It offers three varieties of password assault, brute-pressure attack, brute-power attack with mask, and dictionary attack. You should utilize either of the attack on your situation to effectively crack the password in a time as quick as possible.
an all-in-one password recovery solution for recovering all kinds of misplaced or forgotten passwords for Microsoft Word paperwork, Microsoft Excel spreadsheets, Microsoft Entry databases. It additionally removes each the "Password to Open" and "Password to Edit" for you. It offers three varieties of password assault, brute-pressure attack, brute-power attack with mask, and dictionary attack. You should utilize either of the attack on your situation to effectively crack the password in a time as quick as possible. One of many different findings in different parts of the winrar for mac information. Usually easier to download large recordsdata broken on this case. Unpacking file, they must assume that every process is a tough search of hope, it is typically sufficient to subscribers. This is among the recordsdata to decompress, merely unzip the file and thereby maintain the rest. In any case, no need for users to take part in the reconstruction of the file there. Because the video and audio file types which may be too giant to be suitable for them.
One of many different findings in different parts of the winrar for mac information. Usually easier to download large recordsdata broken on this case. Unpacking file, they must assume that every process is a tough search of hope, it is typically sufficient to subscribers. This is among the recordsdata to decompress, merely unzip the file and thereby maintain the rest. In any case, no need for users to take part in the reconstruction of the file there. Because the video and audio file types which may be too giant to be suitable for them.
Thunderbird And Hotmail
LA (AP) — Microsoft Corp., which has skewered rival Google Inc. for going by means of customer e-mails to ship ads, acknowledged it had searched e-mails in a blogger's Hotmail account to trace down who was leaking company secrets and techniques.
 PrimeMail is one other free email redirect provider that's suitable for forwarding to your Hotmail account or other mail account. It has three options so that you can choose. 1) Use Prime mail solely for forwarding electronic mail to Hotmail e mail account or where you wish all of your mails forwarded 2) Create a Prime mail account where you can use it to ship /receive inside Prime mail or auto electronic mail redirect your e-mail to a different address. With this selection, your incoming mails will likely be retained in your Prime mail account and you will have to access your electronic mail account and capable of delete every mail manually.
PrimeMail is one other free email redirect provider that's suitable for forwarding to your Hotmail account or other mail account. It has three options so that you can choose. 1) Use Prime mail solely for forwarding electronic mail to Hotmail e mail account or where you wish all of your mails forwarded 2) Create a Prime mail account where you can use it to ship /receive inside Prime mail or auto electronic mail redirect your e-mail to a different address. With this selection, your incoming mails will likely be retained in your Prime mail account and you will have to access your electronic mail account and capable of delete every mail manually. The uploading pace of pages is the plus point for yahoo and many people are using this service resulting from its pace and its excellent options that are being provided by yahoo whereas chatting and searching as effectively. Comparable case is with the Gmail that it's getting fame day-to-day on account of its fast uploading pace and its attachment facility that is being acknowledged all over the world. Gmail is the brand new project and it is constantly progressing and resulting from its progress people are getting a bundle of advantages. Now its up-to you that with which service you need to go?
The uploading pace of pages is the plus point for yahoo and many people are using this service resulting from its pace and its excellent options that are being provided by yahoo whereas chatting and searching as effectively. Comparable case is with the Gmail that it's getting fame day-to-day on account of its fast uploading pace and its attachment facility that is being acknowledged all over the world. Gmail is the brand new project and it is constantly progressing and resulting from its progress people are getting a bundle of advantages. Now its up-to you that with which service you need to go? In case you still aren't profitable, don't digress, there may be one final choice. The final and most successful way of finding Hotmail electronic mail addresses is to use a reverse electronic mail lookup service. There are websites that have databases of peoples electronic mail addresses. Using these services all you want is someones title and state and it'll return back a listing of email addresses with loads of other data like their address and phone quantity. Or you possibly can search for an e-mail tackle and it'll return the title and handle related to that electronic mail handle. A lot of these databases are the best choice for finding somebody's Hotmail
In case you still aren't profitable, don't digress, there may be one final choice. The final and most successful way of finding Hotmail electronic mail addresses is to use a reverse electronic mail lookup service. There are websites that have databases of peoples electronic mail addresses. Using these services all you want is someones title and state and it'll return back a listing of email addresses with loads of other data like their address and phone quantity. Or you possibly can search for an e-mail tackle and it'll return the title and handle related to that electronic mail handle. A lot of these databases are the best choice for finding somebody's Hotmail Since there may be certainly a directory of all Hotmail e-mail deal with, the search will not be difficult within the least. The one one factor to be careful for when looking for other people's e-mail addresses is that they're updated. An effective way to do this is to see if they've more than one e mail address listed by their identify once you search for them. The only bad thing about it all is that it may well get fairly confusing if there may be multiple tackle. The other possibility is to make use of a reverse electronic mail handle seek for discovering who you might be in search of. They're free, so there isn't any money to be spent on them. They normally work very well and lead you straight to the particular person's e mail handle. Hopefully, with Hotmail , that will not be essential.
Since there may be certainly a directory of all Hotmail e-mail deal with, the search will not be difficult within the least. The one one factor to be careful for when looking for other people's e-mail addresses is that they're updated. An effective way to do this is to see if they've more than one e mail address listed by their identify once you search for them. The only bad thing about it all is that it may well get fairly confusing if there may be multiple tackle. The other possibility is to make use of a reverse electronic mail handle seek for discovering who you might be in search of. They're free, so there isn't any money to be spent on them. They normally work very well and lead you straight to the particular person's e mail handle. Hopefully, with Hotmail , that will not be essential.
Reverse E-mail Search To Determine A Craigs List Stalker
I have Windows eight and when I click on on Hotmail after which inbox, it goes right to my inbox. No username and no password. Anyone page posts can access my Hotmail on my computer. How do I get it to ask for my username and password at all times?
In case your account has been hijacked, it is vitally easy to search out things back on manner. First take a start by making an attempt to log in to your account. At this phase, a blocked account might be diverted to a fresh web page, now your account has been blocked, which essentially explains why the account has been blocked and what you will have to do to renovate entry. In any other case, should you've observed unusual behaviour or can't register because you could have doubts about your account and now click cannot entry your account? Option on the login display screen and chase the suitable options. This process begins by Microsoft sending a affirmation code to your mobile phone or non-obligatory e-mail handle.
Windows Live Hotmail lets you send and receive email messages for college, work or private purposes. Hotmail often works the best way you want it to, however when you've an issue or question, you wish to contact someone who will help you. If the Hotmail Regularly Requested Questions web page doesn't solve your problem, it's possible to ship an email to the Home windows Live Hotmail assist staff. You will typically obtain a response to your question within 24 hours.
 Secondly, it is now extra necessary than ever to take care of your bounces as soon as possible and maintain a clean mailing checklist. If a message constantly bounces, remove that e mail deal with out of your checklist. In the event you continue emailing to dangerous addresses, your IP will finish by being blacklisted and your emails will not delivered to subscribers. It was just a bad email advertising and marketing “etiquette” to send to non-existent emails, however as you see it is really self-harmful now.
Yahoo wins hands down on this area. The system has a selection of Basic, higher for slower connection speeds, and All New Mail. The extra advanced interface is the best on the Internet. Particularly helpful is the Tabs system. Need a new e mail and also you get a brand new tab. Do a search of e-mail and you get a brand new tab so you possibly can swap between all the things with ease. Hotmail by comparability is irritating. In case you are in the middle of composing a new e mail and need to check one thing in an earlier e mail the only way is to reserve it as a draft and come back to it later. Yahoo is much simpler and quicker.
It also implies that if individuals aren't reading at all – not opening any emails – that it is okay, in reality it's important, to stop emailing them. No matter whether the CAN-SPAM Act applies to you or not, it's higher to have an e-mail record of 10,000 people who actually care and are interested, than to fake to have an inventory of one hundred,000 – ninety% of whom aren't paying consideration. Fairly soon, the ninety% will get you flagged as spam and then even the ten% will not be capable to learn what you ship them any more. Getting actual
Secondly, it is now extra necessary than ever to take care of your bounces as soon as possible and maintain a clean mailing checklist. If a message constantly bounces, remove that e mail deal with out of your checklist. In the event you continue emailing to dangerous addresses, your IP will finish by being blacklisted and your emails will not delivered to subscribers. It was just a bad email advertising and marketing “etiquette” to send to non-existent emails, however as you see it is really self-harmful now.
Yahoo wins hands down on this area. The system has a selection of Basic, higher for slower connection speeds, and All New Mail. The extra advanced interface is the best on the Internet. Particularly helpful is the Tabs system. Need a new e mail and also you get a brand new tab. Do a search of e-mail and you get a brand new tab so you possibly can swap between all the things with ease. Hotmail by comparability is irritating. In case you are in the middle of composing a new e mail and need to check one thing in an earlier e mail the only way is to reserve it as a draft and come back to it later. Yahoo is much simpler and quicker.
It also implies that if individuals aren't reading at all – not opening any emails – that it is okay, in reality it's important, to stop emailing them. No matter whether the CAN-SPAM Act applies to you or not, it's higher to have an e-mail record of 10,000 people who actually care and are interested, than to fake to have an inventory of one hundred,000 – ninety% of whom aren't paying consideration. Fairly soon, the ninety% will get you flagged as spam and then even the ten% will not be capable to learn what you ship them any more. Getting actual
Portland International Airport
 Not accessible in all areas. Restrictions apply. Hotspots declare primarily based on June 21, 2013 research by Allion Take a look at Labs, Inc. XFINITY WiFi is included for XFINITY Web Efficiency tiers and above. Not obtainable with Financial system Web. Requires appropriate WiFi-enabled laptop or cellular machine. Hotspots accessible in select places only. Name 1-800-XFINITY for more details. Not accessible in all areas. Restrictions apply. Hotspots declare primarily based on June 21, 2013 research by Allion Take a look at Labs, Inc. XFINITY WiFi is included for XFINITY Web Efficiency tiers and above. Not obtainable with Financial system Web. Requires appropriate WiFi-enabled laptop or cellular machine. Hotspots accessible in select places only. Name 1-800-XFINITY for more details. If you need data or voice service and there isn't any Wi-Fi close by, just purchase a pass. It's as straightforward as shopping for a track. For as little as $1.ninety nine, you may bounce on the mobile network (offered on the Nationwide Dash Network), do what you have to, and once you're back on Wi-Fi it's all free once more. If you need extra or just do not need to give it some thought, we additionally offer bigger passes to maintain you related all the time. But there's by no means any contract or obligation. It's all the time up to you. SEE ACCESSIBLE PASSES
If you need data or voice service and there isn't any Wi-Fi close by, just purchase a pass. It's as straightforward as shopping for a track. For as little as $1.ninety nine, you may bounce on the mobile network (offered on the Nationwide Dash Network), do what you have to, and once you're back on Wi-Fi it's all free once more. If you need extra or just do not need to give it some thought, we additionally offer bigger passes to maintain you related all the time. But there's by no means any contract or obligation. It's all the time up to you. SEE ACCESSIBLE PASSES This isn't to say that AT&T's and Xfinity's networks are insecure in themselves. They are just frequent enough to provide someone with evil in thoughts a technique to solid a large net for potential victims over Wi-Fi. The identical instruments I used to spoof Xfinity might be set to mechanically reply to a victim's phone as any Wi-Fi entry level they've trusted. That's because of the probe requests generated by smartphones and Wi-Fi—whenever you flip on your telephone's Wi-Fi adapter, it is going to seek out any community you've got ever linked to that it was not told to neglect.
This isn't to say that AT&T's and Xfinity's networks are insecure in themselves. They are just frequent enough to provide someone with evil in thoughts a technique to solid a large net for potential victims over Wi-Fi. The identical instruments I used to spoof Xfinity might be set to mechanically reply to a victim's phone as any Wi-Fi entry level they've trusted. That's because of the probe requests generated by smartphones and Wi-Fi—whenever you flip on your telephone's Wi-Fi adapter, it is going to seek out any community you've got ever linked to that it was not told to neglect. In addition to the phased WiFi implementation, Harlem Youngsters's Zone shall be increasing consciousness and network use amongst Harlem residents, companies, and visitors. As part of this schooling and outreach process, Harlem Youngsters's Zone's high school college students are engaged in a contest to develop a reputation and emblem for the network later this month. The printing of the promotional supplies which are selected has been donated by Showtime Networks and Peachtree Enterprises.
In addition to the phased WiFi implementation, Harlem Youngsters's Zone shall be increasing consciousness and network use amongst Harlem residents, companies, and visitors. As part of this schooling and outreach process, Harlem Youngsters's Zone's high school college students are engaged in a contest to develop a reputation and emblem for the network later this month. The printing of the promotional supplies which are selected has been donated by Showtime Networks and Peachtree Enterprises. Wi-Fi supplies service in personal houses, businesses, in addition to in public areas at Wi-Fi hotspots arrange both free-of-cost or commercially, usually utilizing a captive portal webpage for access. Organizations and businesses , comparable to airports, lodges, and eating places, typically provide free-use hotspots to draw prospects. Fanatics or authorities who wish to present services and even to advertise business in chosen areas typically provide free Wi-Fi access.
Wi-Fi supplies service in personal houses, businesses, in addition to in public areas at Wi-Fi hotspots arrange both free-of-cost or commercially, usually utilizing a captive portal webpage for access. Organizations and businesses , comparable to airports, lodges, and eating places, typically provide free-use hotspots to draw prospects. Fanatics or authorities who wish to present services and even to advertise business in chosen areas typically provide free Wi-Fi access.
|
Cracking Of Wi-fi Networks
 Wireshark is a packet sniffer and network site visitors analyser that may run on all standard working methods, but help for the seize of wireless traffic is restricted. It is free and open supply. Decoding and analysing wi-fi site visitors isn't the foremost perform of Wireshark, but it can give outcomes that cannot be obtained with different packages. Wireshark requires sufficient knowledge of the community protocols to acquire a full evaluation of the visitors, nevertheless. 14 Analysers of AirMagnet edit
Wireshark is a packet sniffer and network site visitors analyser that may run on all standard working methods, but help for the seize of wireless traffic is restricted. It is free and open supply. Decoding and analysing wi-fi site visitors isn't the foremost perform of Wireshark, but it can give outcomes that cannot be obtained with different packages. Wireshark requires sufficient knowledge of the community protocols to acquire a full evaluation of the visitors, nevertheless. 14 Analysers of AirMagnet edit A wi-fi router with WPS DISABLED, a NON-DEFAULT SSID, no wireless machine using the network EVER and a WPA2 password of over 12 characters consisting of each random upper and decrease case letters and numbers that DO NOT spell a word, name or have any pattern, CAN'T BE CRACKED. Cracking of wireless networks is the defeating of safety devices in Wi-fi native-area networks Wi-fi native-area networks(WLANs) – also called Wi-Fi networks are inherently susceptible to security lapses that wired networks are exempt from. 1 In case you have a COMPUTER with a wireless community card , then you have to have seen many networks around you. Sadly most of those networks are secured with a network safety key. Begin scanning for wireless networks. Enable MAC Tackle guidelines.
A wi-fi router with WPS DISABLED, a NON-DEFAULT SSID, no wireless machine using the network EVER and a WPA2 password of over 12 characters consisting of each random upper and decrease case letters and numbers that DO NOT spell a word, name or have any pattern, CAN'T BE CRACKED. Cracking of wireless networks is the defeating of safety devices in Wi-fi native-area networks Wi-fi native-area networks(WLANs) – also called Wi-Fi networks are inherently susceptible to security lapses that wired networks are exempt from. 1 In case you have a COMPUTER with a wireless community card , then you have to have seen many networks around you. Sadly most of those networks are secured with a network safety key. Begin scanning for wireless networks. Enable MAC Tackle guidelines. Take, for instance, the tons of of millions of WiFi networks in use all around the world. If they're like those within vary of my office, most of them are protected by the WiFi Protected Access or WiFi Protected Access 2 security protocols. In theory, these protections prevent hackers and different unauthorized people from accessing wireless networks or even Pirater mot de passe WIFI viewing traffic sent over them, but only when finish users choose robust passwords. I used to be curious how simple it will be to crack these passcodes using the superior hardware menus and techniques that have change into available over the past 5 years. What I discovered wasn't encouraging.
Take, for instance, the tons of of millions of WiFi networks in use all around the world. If they're like those within vary of my office, most of them are protected by the WiFi Protected Access or WiFi Protected Access 2 security protocols. In theory, these protections prevent hackers and different unauthorized people from accessing wireless networks or even Pirater mot de passe WIFI viewing traffic sent over them, but only when finish users choose robust passwords. I used to be curious how simple it will be to crack these passcodes using the superior hardware menus and techniques that have change into available over the past 5 years. What I discovered wasn't encouraging. Little question, this neighbor ought to have modified his password way back, but there's a lot to admire about his safety hygiene nonetheless. By resisting the temptation to make use of a human-readable phrase, he evaded a fair amount of slicing-edge resources dedicated to discovering his passcode. For the reason that code isn't prone to be included in any password cracking phrase lists, the one option to crack it could be to try every eight-character combination of letters and numbers. Such brute-pressure attacks are potential, but in one of the best of worlds they require no less than six days to exhaust all the probabilities when using Amazon's EC2 cloud computing service WPA's use of a highly iterated implementation of the PBKDF2 perform makes such cracks even tougher.
Little question, this neighbor ought to have modified his password way back, but there's a lot to admire about his safety hygiene nonetheless. By resisting the temptation to make use of a human-readable phrase, he evaded a fair amount of slicing-edge resources dedicated to discovering his passcode. For the reason that code isn't prone to be included in any password cracking phrase lists, the one option to crack it could be to try every eight-character combination of letters and numbers. Such brute-pressure attacks are potential, but in one of the best of worlds they require no less than six days to exhaust all the probabilities when using Amazon's EC2 cloud computing service WPA's use of a highly iterated implementation of the PBKDF2 perform makes such cracks even tougher. AirMagnet Laptop Analyser and AirMagnet Handheld Analyser are wireless network analysis instruments made by AirMagnet The corporate started with the Handheld Analyser, which was very appropriate for surveying sites the place wireless networks had been deployed as well as for finding rogue access factors. The Laptop computer Analyser was launched as a result of the hand-held product was impractical for the reconnaissance of huge Pirater WIFI areas. These commercial analysers most likely supply the very best combination of powerful analysis and simple person interface. Nonetheless, they don't seem to be as nicely adapted to the needs of a wardriver as some of the free applications. 15 Airopeek edit
AirMagnet Laptop Analyser and AirMagnet Handheld Analyser are wireless network analysis instruments made by AirMagnet The corporate started with the Handheld Analyser, which was very appropriate for surveying sites the place wireless networks had been deployed as well as for finding rogue access factors. The Laptop computer Analyser was launched as a result of the hand-held product was impractical for the reconnaissance of huge Pirater WIFI areas. These commercial analysers most likely supply the very best combination of powerful analysis and simple person interface. Nonetheless, they don't seem to be as nicely adapted to the needs of a wardriver as some of the free applications. 15 Airopeek edit
 Wireshark is a packet sniffer and network site visitors analyser that may run on all standard working methods, but help for the seize of wireless traffic is restricted. It is free and open supply. Decoding and analysing wi-fi site visitors isn't the foremost perform of Wireshark, but it can give outcomes that cannot be obtained with different packages. Wireshark requires sufficient knowledge of the community protocols to acquire a full evaluation of the visitors, nevertheless. 14 Analysers of AirMagnet edit
Wireshark is a packet sniffer and network site visitors analyser that may run on all standard working methods, but help for the seize of wireless traffic is restricted. It is free and open supply. Decoding and analysing wi-fi site visitors isn't the foremost perform of Wireshark, but it can give outcomes that cannot be obtained with different packages. Wireshark requires sufficient knowledge of the community protocols to acquire a full evaluation of the visitors, nevertheless. 14 Analysers of AirMagnet edit A wi-fi router with WPS DISABLED, a NON-DEFAULT SSID, no wireless machine using the network EVER and a WPA2 password of over 12 characters consisting of each random upper and decrease case letters and numbers that DO NOT spell a word, name or have any pattern, CAN'T BE CRACKED. Cracking of wireless networks is the defeating of safety devices in Wi-fi native-area networks Wi-fi native-area networks(WLANs) – also called Wi-Fi networks are inherently susceptible to security lapses that wired networks are exempt from. 1 In case you have a COMPUTER with a wireless community card , then you have to have seen many networks around you. Sadly most of those networks are secured with a network safety key. Begin scanning for wireless networks. Enable MAC Tackle guidelines.
A wi-fi router with WPS DISABLED, a NON-DEFAULT SSID, no wireless machine using the network EVER and a WPA2 password of over 12 characters consisting of each random upper and decrease case letters and numbers that DO NOT spell a word, name or have any pattern, CAN'T BE CRACKED. Cracking of wireless networks is the defeating of safety devices in Wi-fi native-area networks Wi-fi native-area networks(WLANs) – also called Wi-Fi networks are inherently susceptible to security lapses that wired networks are exempt from. 1 In case you have a COMPUTER with a wireless community card , then you have to have seen many networks around you. Sadly most of those networks are secured with a network safety key. Begin scanning for wireless networks. Enable MAC Tackle guidelines. Take, for instance, the tons of of millions of WiFi networks in use all around the world. If they're like those within vary of my office, most of them are protected by the WiFi Protected Access or WiFi Protected Access 2 security protocols. In theory, these protections prevent hackers and different unauthorized people from accessing wireless networks or even Pirater mot de passe WIFI viewing traffic sent over them, but only when finish users choose robust passwords. I used to be curious how simple it will be to crack these passcodes using the superior hardware menus and techniques that have change into available over the past 5 years. What I discovered wasn't encouraging.
Take, for instance, the tons of of millions of WiFi networks in use all around the world. If they're like those within vary of my office, most of them are protected by the WiFi Protected Access or WiFi Protected Access 2 security protocols. In theory, these protections prevent hackers and different unauthorized people from accessing wireless networks or even Pirater mot de passe WIFI viewing traffic sent over them, but only when finish users choose robust passwords. I used to be curious how simple it will be to crack these passcodes using the superior hardware menus and techniques that have change into available over the past 5 years. What I discovered wasn't encouraging. Little question, this neighbor ought to have modified his password way back, but there's a lot to admire about his safety hygiene nonetheless. By resisting the temptation to make use of a human-readable phrase, he evaded a fair amount of slicing-edge resources dedicated to discovering his passcode. For the reason that code isn't prone to be included in any password cracking phrase lists, the one option to crack it could be to try every eight-character combination of letters and numbers. Such brute-pressure attacks are potential, but in one of the best of worlds they require no less than six days to exhaust all the probabilities when using Amazon's EC2 cloud computing service WPA's use of a highly iterated implementation of the PBKDF2 perform makes such cracks even tougher.
Little question, this neighbor ought to have modified his password way back, but there's a lot to admire about his safety hygiene nonetheless. By resisting the temptation to make use of a human-readable phrase, he evaded a fair amount of slicing-edge resources dedicated to discovering his passcode. For the reason that code isn't prone to be included in any password cracking phrase lists, the one option to crack it could be to try every eight-character combination of letters and numbers. Such brute-pressure attacks are potential, but in one of the best of worlds they require no less than six days to exhaust all the probabilities when using Amazon's EC2 cloud computing service WPA's use of a highly iterated implementation of the PBKDF2 perform makes such cracks even tougher. AirMagnet Laptop Analyser and AirMagnet Handheld Analyser are wireless network analysis instruments made by AirMagnet The corporate started with the Handheld Analyser, which was very appropriate for surveying sites the place wireless networks had been deployed as well as for finding rogue access factors. The Laptop computer Analyser was launched as a result of the hand-held product was impractical for the reconnaissance of huge Pirater WIFI areas. These commercial analysers most likely supply the very best combination of powerful analysis and simple person interface. Nonetheless, they don't seem to be as nicely adapted to the needs of a wardriver as some of the free applications. 15 Airopeek edit
AirMagnet Laptop Analyser and AirMagnet Handheld Analyser are wireless network analysis instruments made by AirMagnet The corporate started with the Handheld Analyser, which was very appropriate for surveying sites the place wireless networks had been deployed as well as for finding rogue access factors. The Laptop computer Analyser was launched as a result of the hand-held product was impractical for the reconnaissance of huge Pirater WIFI areas. These commercial analysers most likely supply the very best combination of powerful analysis and simple person interface. Nonetheless, they don't seem to be as nicely adapted to the needs of a wardriver as some of the free applications. 15 Airopeek edit
How Do I Set My Wi-fi Community To Be Private Instead Of Public?
 These pages review the forms of designs, equipment, protocols and different applied sciences important to constructing pc networks. You will find out how home and different private networks, public hotspots and the Web perform.
The subsequent technology of excessive-pace wi-fi networking customary, the draft 802.11n standard specifies a most knowledge switch price of up to 540Mbps. It is constructed on the premise of earlier 802.eleven requirements with the addition of MIMO (a number of-input a number of-output) know-how. It's required to be backward compatible and interoperable with 802.11b/g gadgets. The final 802.11n specification is expected to be approved in 2007 in order that modern 802.11n-supporting merchandise can provide completely different most information transfer charges (e.g. 270Mbps, 300Mbps)
These pages review the forms of designs, equipment, protocols and different applied sciences important to constructing pc networks. You will find out how home and different private networks, public hotspots and the Web perform.
The subsequent technology of excessive-pace wi-fi networking customary, the draft 802.11n standard specifies a most knowledge switch price of up to 540Mbps. It is constructed on the premise of earlier 802.eleven requirements with the addition of MIMO (a number of-input a number of-output) know-how. It's required to be backward compatible and interoperable with 802.11b/g gadgets. The final 802.11n specification is expected to be approved in 2007 in order that modern 802.11n-supporting merchandise can provide completely different most information transfer charges (e.g. 270Mbps, 300Mbps) However, sure forms of equipment, reminiscent of lighting tools and industrial electrical gear, are usually not lined by these laws. In addition, digital gear which does conform to authorities requirements can still intervene with wireless systems if sure precautions should not taken. Age, put on and inadequate maintenance can also take their toll on gear and cause it to ultimately grow to be a supply of interference. In some cases, gear was manufactured before the federal government regulations were in place, and there may have been no effort made to cut back interference.
The existence of different close by wi-fi methods is a chance that must be thought-about. Wi-fi systems can interfere with one another at distances of 2000 feet (600 meters) or extra. It isn't highly uncommon to have interference from another wireless system in a unique area of a building or facility, at a house of worship down the street, or at a membership across the corner. Tv and radio information crews additionally use wireless microphones extensively, so temporary interference could occur near the scene of newsworthy events.
However, sure forms of equipment, reminiscent of lighting tools and industrial electrical gear, are usually not lined by these laws. In addition, digital gear which does conform to authorities requirements can still intervene with wireless systems if sure precautions should not taken. Age, put on and inadequate maintenance can also take their toll on gear and cause it to ultimately grow to be a supply of interference. In some cases, gear was manufactured before the federal government regulations were in place, and there may have been no effort made to cut back interference.
The existence of different close by wi-fi methods is a chance that must be thought-about. Wi-fi systems can interfere with one another at distances of 2000 feet (600 meters) or extra. It isn't highly uncommon to have interference from another wireless system in a unique area of a building or facility, at a house of worship down the street, or at a membership across the corner. Tv and radio information crews additionally use wireless microphones extensively, so temporary interference could occur near the scene of newsworthy events. To have a wireless network, you need both a wireless card to your laptop and a wireless access level to take the sign from the air and send it to its vacation spot. The wi-fi card you buy should help multiple sorts of wi-fi networks, and most cards that you just purchase at present will. Any pc with wi-fi functionality that's in vary of the sign can achieve entry to the Internet. Unless you're taking certain steps, someone can entry the information in your pc as properly. Types of Wi-fi
To have a wireless network, you need both a wireless card to your laptop and a wireless access level to take the sign from the air and send it to its vacation spot. The wi-fi card you buy should help multiple sorts of wi-fi networks, and most cards that you just purchase at present will. Any pc with wi-fi functionality that's in vary of the sign can achieve entry to the Internet. Unless you're taking certain steps, someone can entry the information in your pc as properly. Types of Wi-fi
 These pages review the forms of designs, equipment, protocols and different applied sciences important to constructing pc networks. You will find out how home and different private networks, public hotspots and the Web perform.
The subsequent technology of excessive-pace wi-fi networking customary, the draft 802.11n standard specifies a most knowledge switch price of up to 540Mbps. It is constructed on the premise of earlier 802.eleven requirements with the addition of MIMO (a number of-input a number of-output) know-how. It's required to be backward compatible and interoperable with 802.11b/g gadgets. The final 802.11n specification is expected to be approved in 2007 in order that modern 802.11n-supporting merchandise can provide completely different most information transfer charges (e.g. 270Mbps, 300Mbps)
These pages review the forms of designs, equipment, protocols and different applied sciences important to constructing pc networks. You will find out how home and different private networks, public hotspots and the Web perform.
The subsequent technology of excessive-pace wi-fi networking customary, the draft 802.11n standard specifies a most knowledge switch price of up to 540Mbps. It is constructed on the premise of earlier 802.eleven requirements with the addition of MIMO (a number of-input a number of-output) know-how. It's required to be backward compatible and interoperable with 802.11b/g gadgets. The final 802.11n specification is expected to be approved in 2007 in order that modern 802.11n-supporting merchandise can provide completely different most information transfer charges (e.g. 270Mbps, 300Mbps) However, sure forms of equipment, reminiscent of lighting tools and industrial electrical gear, are usually not lined by these laws. In addition, digital gear which does conform to authorities requirements can still intervene with wireless systems if sure precautions should not taken. Age, put on and inadequate maintenance can also take their toll on gear and cause it to ultimately grow to be a supply of interference. In some cases, gear was manufactured before the federal government regulations were in place, and there may have been no effort made to cut back interference.
The existence of different close by wi-fi methods is a chance that must be thought-about. Wi-fi systems can interfere with one another at distances of 2000 feet (600 meters) or extra. It isn't highly uncommon to have interference from another wireless system in a unique area of a building or facility, at a house of worship down the street, or at a membership across the corner. Tv and radio information crews additionally use wireless microphones extensively, so temporary interference could occur near the scene of newsworthy events.
However, sure forms of equipment, reminiscent of lighting tools and industrial electrical gear, are usually not lined by these laws. In addition, digital gear which does conform to authorities requirements can still intervene with wireless systems if sure precautions should not taken. Age, put on and inadequate maintenance can also take their toll on gear and cause it to ultimately grow to be a supply of interference. In some cases, gear was manufactured before the federal government regulations were in place, and there may have been no effort made to cut back interference.
The existence of different close by wi-fi methods is a chance that must be thought-about. Wi-fi systems can interfere with one another at distances of 2000 feet (600 meters) or extra. It isn't highly uncommon to have interference from another wireless system in a unique area of a building or facility, at a house of worship down the street, or at a membership across the corner. Tv and radio information crews additionally use wireless microphones extensively, so temporary interference could occur near the scene of newsworthy events. To have a wireless network, you need both a wireless card to your laptop and a wireless access level to take the sign from the air and send it to its vacation spot. The wi-fi card you buy should help multiple sorts of wi-fi networks, and most cards that you just purchase at present will. Any pc with wi-fi functionality that's in vary of the sign can achieve entry to the Internet. Unless you're taking certain steps, someone can entry the information in your pc as properly. Types of Wi-fi
To have a wireless network, you need both a wireless card to your laptop and a wireless access level to take the sign from the air and send it to its vacation spot. The wi-fi card you buy should help multiple sorts of wi-fi networks, and most cards that you just purchase at present will. Any pc with wi-fi functionality that's in vary of the sign can achieve entry to the Internet. Unless you're taking certain steps, someone can entry the information in your pc as properly. Types of Wi-fi
